
Multiple audio leaks have surfaced in recent weeks that made headlines. These leaks uncovered discussions that took place in the Prime Minister's Office on policy issues involving the cabinet and other top government officials.
Open Source Intelligence Insider (@OSINT Insider on Twitter) claims that the audio files that have been made public are a collection of discussions that lasted 140 hours and included 100 8 GB files. The full collection of recordings, which have been on sale since August 20th, demanded $3.45 million. Additionally, according to @OSINT Insider, the phone calls made from the PM House were not secure.
The saga surrounding the audio leaks from the Pakistani Prime Minister's Office is set to raise more questions since a message on the dark web has spurred the release of all the audio files that have been compromised. The country's intelligence sources, however, are unable to confirm the veracity of these assertions. On September 24, a number of files that had purportedly been taped in the PMO surfaced online. They appeared to depict Sharif and other ministers discussing business. In at least one leak, Maryam Nawaz Sharif, Vice President of the ruling Pakistan Muslim League-Nawaz party was audible.
As soon as the data hit Pakistani social media, Information Minister Marriyum Aurangzeb downplayed the situation, stating that it included nothing unlawful or incriminating.
The prime minister described the leaks as a "very significant cyber security lapse" and ordered the constitution of a strong commission to look into the matter.
This raises a lot of questions. Foreign dignitaries visiting Pakistan would be hesitant to talk at the PM House? They will pause before saying anything delicate. They will ask themselves a hundred times whether these conversations are being recorded.
The country's highest executive office has been "spied upon" in a "severe breach of cyber security."
Despite established procedures, intelligence agencies are unaware of how the PM House has been bugged for months. Furthermore, according to sources, the Intelligence Bureau told Pakistan's Prime Minister Shehbaz Sharif about the hacking that came to light a few weeks ago. The dark web announced that it would soon release additional information. "I will be providing ALL files sooner for undisclosed reasons," the website claimed. There will be no more haggling and offers to sell the data will be taken. According to the dark web, the audios contain interactions with journalists, chats with government officials, conversations with the top military leaders and personnel, personal and official deals, and interactions between the first family and other families, among other types of material. Additionally, it stated that it has audio recordings of talks that may be used as evidence. These discussions included those with serving judicial appointments, with foreign dignitaries, and instructions or commands given by staff. "Hopefully this release will bring betterment to Pakistan," the dark web letter said.
According to a hacker, Aamer Liaquat and Judge Arshad Malik were slain by Imran Khan. The hacker further asserted that Imran Khan's order locked the former DG FIA Bashir Memon in the PM House restroom. Imran Khan vowed to make Memon follow his instructions. In response to the claim of the hacker, Memon acknowledged that Khan used abusive language toward PML-N Vice President Maryam Nawaz, which had enraged him. Memon continued that at this point, PM Azam Khan's then-principal secretary grabbed his hand, led him out of the room, and locked him in the restroom. Then, according to Memon, "Azam Khan scolded me for my conduct with the prime minister." A powerful committee has been established in order to investigate audio leaks from the PM House that have called into question the government's cyber security.
Multiple audio leaks have also been shared online, igniting fresh political debate around the PTI's claim of a US conspiracy. In one of the audio leaks, the former prime minister was apparently heard discussing how to utilize the US cypher problem to further the party's narrative. A private TV channel claimed that the committee, which consists of federal ministers and the leaders of security services, will be in charge of overseeing the inquiry into audio leaks from the Prime Minister's House (PMO). Azam Nazir Tarar, the minister of law and justice, Sherry Rehman, the minister of climate change, Asad Mehmood, the minister of communications, Aminul Haque, the director-general of inter-services intelligence (ISI), the director-general of the intelligence bureau (IB), and the cabinet secretary will also serve on the high-level committee, which will be led by interior minister Rana Sanaullah. The investigation will also include co-opted members who are technical specialists from the Pakistan Telecom Authority, FIA, ISI, and National Information Technology Board.
The committee will be in charge of monitoring and analyzing the PM Office cyber security breach and making sure that it is fully investigated within seven days. The notification stated that "[they] will review the current cyber security protocols of the Prime Minister's House/Office and suggest immediate measures and an action plan to develop foolproof security systems and a digital eco-system that insulates the PM's Office/cyberspace House from all kinds of intrusion (in seven days)". The committee will review current cybersecurity and e-safety policies and procedures, analyze the current vulnerabilities and strengths of government agencies, and reevaluate the dangers posed by various electronic devices such as tablets, smartphones, WiFi, and other cyber devices. "And offer ways to strengthen government agencies' resistance against cyberattacks."
The committee has also been given instructions by the prime minister to establish a legal framework for a secure cyber environment for government offices and to make suggestions within 15 days on how to safeguard sensitive data from crucial ministries.
What is the Deep and Dark Web?
The dark web is a secret network of websites that can only be accessed with a specialized web browser. It is used to maintain the privacy and anonymity of internet activity, which is useful for both legal and illegal uses. The use of it for extremely criminal activities has also been reported, even though some people use it to avoid government censorship. There are millions of websites, databases, and servers that are all active around the clock on the vast Internet. However, the sites that can be accessed using search engines like Google and Yahoo are only the tip of the iceberg when it comes to the so-called "visible" Internet (also known as the surface web or open web). The non-visible Web is surrounded by a number of terminologies, but if you're going to venture off the beaten track, it's important to understand how they differ.
The "visible" surface layer is the open web, often known as the surface web. The open web would be the top part that is above the sea if we were to continue to picture the full web as an iceberg. According to statistics, this group of websites and data accounts for less than 5% of the entire internet. These are all frequently visited public-facing websites that can be accessed with conventional browsers like Google Chrome, Internet Explorer, and Firefox. Websites are typically identified by registration operators like ".com" and ".org" and are simple to find using well-known search engines. Because search engines can index the web through visible links (a technique known as "crawling" because the search engine moves through the web like a spider), it is possible to locate surface web websites. About 90% of all websites are found on the deep web, which is underground. This would be a portion of an iceberg that was submerged and was much larger than the web on the surface. In fact, the size of this hidden network makes it impossible to determine precisely how many pages or websites are open at any given time. If we continue with the comparison, big search engines could be compared to fishing boats that can only "grab" webpages at the surface. Everything else, including scholarly publications, exclusive databases, and additional illegal content, is out of your grasp. The area of the deep web that is known as the dark web is also included.
Cybersecurity is a big challenge for Pakistan
Pakistan has taken many steps to compete with other nations in the digital arena, but problems with governance, data privacy, and cybersecurity have slowed down its progress. The Global Cybersecurity Index (GCI) placed Pakistan 94th overall and 18th out of 38 Asia-Pacific nations, trailing Bangladesh, Sri Lanka, and India, according to the report "Transforming Digital Government in Pakistan". Recurrent cyberattacks throughout the previous five years are to blame for the low rating. The government hasn't done well when it comes to building trust by guaranteeing the security of citizens' personal information. Numerous Pakistani organizations, including the Federal Board of Revenue (FBR), Careem, PTV Sports, the website of Sindh High Court, Patari, K-Electric, NADRA, PITB, Meezan Bank, and Bank Islami, have experienced cyberattacks, and last month Sensitive data of the Securities and Exchange Commission of Pakistan (SECP) was also stolen.
The research states that gaining the population's trust "requires effective data privacy procedures in the government's public monitoring activities" with regard to figuring out the population and its need to establish a threshold for trust. To that end, the government made advances by enacting the Prevention of Electronic Crimes Act (PECA), 2016, which lays out penalties for offenders or criminals who are accused of gaining unauthorized access to personal data. Through its National Response Centre for Cyber Crime, the Federal Investigation Agency (FIA) also enacts legislation regarding penalties under the PECA filing (NR3C). While the cyber security policy- 2021 must be put into full effect.
Cyber Security Framework
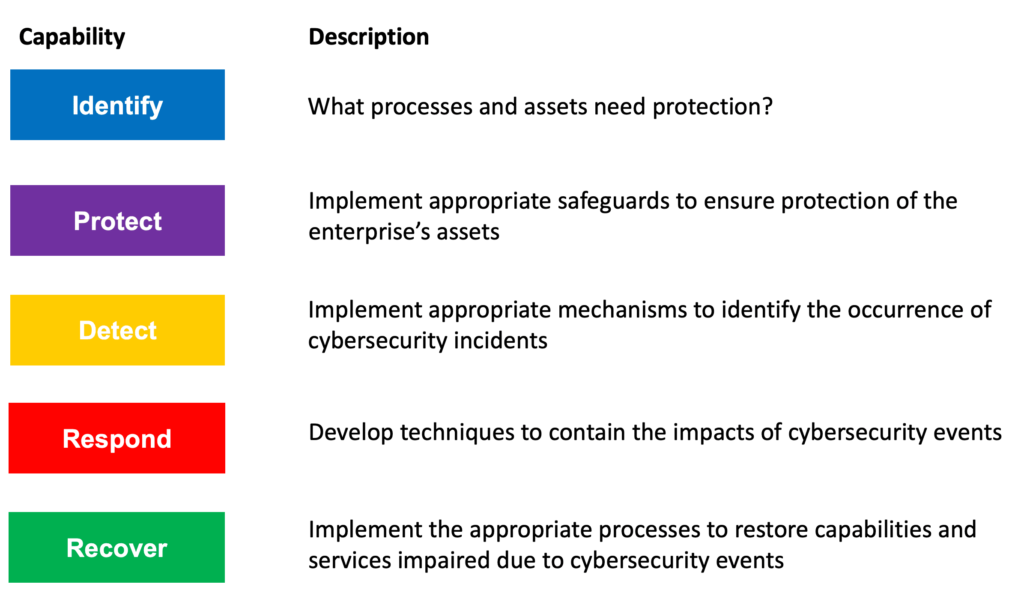
The U.S. Department of Commerce's NIST is the National Institute of Standards and Technology. The NIST Cybersecurity Framework assists companies of all sizes in comprehending, managing, and reducing their cybersecurity risk as well as safeguarding their networks and data.
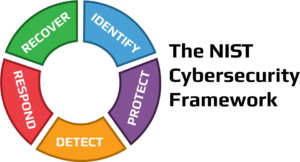
In his executive order for Improving Critical Infrastructure Cybersecurity, former US President Barack Obama called for greater collaboration between the public and private sectors in recognizing, analyzing, and managing cyber risk. In response, the NIST Cybersecurity Framework was developed. NIST has emerged as the gold standard for evaluating cybersecurity maturity, detecting security weaknesses, and adhering to cybersecurity legislation even when compliance is optional.
To assist firms in managing their cybersecurity risks, the Framework incorporates best practices and industry standards. It offers a standard language that enables workers at all organizational levels and at all supply chain nodes to become aware of one another's cybersecurity concerns.
Hacking and precautionary measures for your phone
One or more of these can indicate that your phone has been hacked:
Your phone quickly loses battery. Malicious code can be used by malware and fraudulent apps, which can consume a lot of power.
Your phone is operating unusually slowly. A compromised phone may be giving the hacker's dubious applications complete access to its computing power. Your phone can become quite slow as a result of this. Sometimes the symptoms include unexpected restarts and freezing crashes.
Your other online accounts show unusual behavior. A hacker who gains access to your phone will attempt to take control of your valuable accounts. Look for password reset requests, strange login URLs, or new account signup verifications on social media and in your email.
You discover strange texts or calls in your logs. Your phone may be being tapped by hackers using SMS malware. Alternatively, they can pretend to be you in order to steal private information from your loved ones. Both methods leave traces, like outgoing mail, so keep a watch out.
While there are a number of ways a hacker might access your phone and take sensitive and private data, here are some suggestions to prevent that from happening:
On your phone, install comprehensive security software. Over time, we've developed the good habit of doing this on our laptops and computers. Our phones are not at all. Installing security software on your smartphone could provide you with the first line of defense against attacks as well as some of the additional security features discussed below. Update your mobile device's apps. In addition to installing security software, the main strategy to keep you and your phone safe are to stay up to speed with updates.
Updates can close security holes used by thieves to launch their malware-based attacks. Additionally, those updates can help keep your phone and apps running smoothly while also introducing new, helpful features. Use a VPN to stay safe when traveling. Public Wi-Fi, found in places like hotels, airports, and even libraries, is one way that thieves might access your phone. Since these networks are public, all of your online activities, including banking and password usage, are visible to other users. By using a VPN, you may make a public network private and keep your online activity private from other users.
Make use of a password manager. Another important line of defense is the use of strong, distinctive passwords. The temptation to use (and re-use) shorter passwords arises from the fact that managing the hundreds of strong, unique passwords we need to manage the numerous accounts we have might feel like a chore. Because one password can unlock numerous accounts, hackers adore this situation. Try using a password manager instead, which can both generate these passwords for you and store them securely. One will be present in comprehensive security software. Avoid using public chargers. A public charging station makes charging look so easy and secure. However, some cybercriminals have been found to "juice jack" charging stations by inserting malware. They "jack" your passwords and personal information as you "juice up." How should power on the road be handled then? Consider a portable power source that you can pre-charge or use AA batteries to power. They are reasonably priced and simple to locate.
Keep a vigilant eye on your phone. Additionally, it's crucial to avoid having your phone actually stolen, as some hacks only take place when a phone ends up in the wrong hands. This is an excellent time to lock your phone with a password or PIN and enable device tracking so you can find it if you need to or even remotely wipe it. A step-by-step manual for remotely wiping devices is made available to iOS users by Apple, and an Android user manual is made available by Google. Encrypt your phone. Your calls, messages, and important data can be safeguarded by encrypting the data on your mobile device to prevent hacking. You can scroll to the bottom of Touch ID & Passcode, check if data protection is enabled, and see if your iPhone is encrypted to find out if it is (typically this is automatic if you have a passcode enabled). Depending on the phone model, Android users can automatically encrypt their data.
Lock your SIM card. The SIM card that is used to identify you as the owner and link you to your cellular network can be locked, much like your phone. It keeps your phone from being used on any other network but your own by locking it. If you have one, you can lock your iPhone by following these easy instructions. Go to the manufacturer's website to learn more about other platforms.
When not in use, turn off your Bluetooth and Wi-Fi. Consider it as closing a door that was once open. A dedicated hacker with the right tools can launch a variety of attacks against devices with open and discoverable Wi-Fi and Bluetooth. Similarly, while not a hack, some stores use Bluetooth technology to track your whereabouts within a store for marketing purposes, so turning it off might sometimes preserve your privacy. Both are simple to turn off via your settings, and many smartphones also give you the option to do so from a pull-down menu on your home screen.
Avoid using app stores from outside sources. In order to help ensure that apps are safe and secure, Google Play and Apple's App Store have systems in place to review and vet them. That procedure might not be in place for third-party websites. In reality, as part of a larger deception, certain third-party websites may purposefully host dangerous programs. Even though hackers have developed techniques to get through Google and Apple's review procedures, there is still a much higher probability of downloading a secure program from these sources than from any other. Additionally, Google and Apple swiftly remove harmful programs when they are found, further enhancing the security of their app marketplaces.
Using the built-in phone tapping codes is a quick and simple way to find the problem and solve it. With these fast codes, you can have access to confidential data about the security of your device. Utilizing them is as simple as calling a number; the phone will instantly recognize your actions and provide you with the information. To learn more about these vital cell phone codes and hacks, continue reading:
Open Source Intelligence Insider (@OSINT Insider on Twitter) claims that the audio files that have been made public are a collection of discussions that lasted 140 hours and included 100 8 GB files. The full collection of recordings, which have been on sale since August 20th, demanded $3.45 million. Additionally, according to @OSINT Insider, the phone calls made from the PM House were not secure.
The saga surrounding the audio leaks from the Pakistani Prime Minister's Office is set to raise more questions since a message on the dark web has spurred the release of all the audio files that have been compromised. The country's intelligence sources, however, are unable to confirm the veracity of these assertions. On September 24, a number of files that had purportedly been taped in the PMO surfaced online. They appeared to depict Sharif and other ministers discussing business. In at least one leak, Maryam Nawaz Sharif, Vice President of the ruling Pakistan Muslim League-Nawaz party was audible.
The embarrassing audio leaks caused people to doubt the security measures in place at the PM House -- generally thought to be highly secure location.
As soon as the data hit Pakistani social media, Information Minister Marriyum Aurangzeb downplayed the situation, stating that it included nothing unlawful or incriminating.
The prime minister described the leaks as a "very significant cyber security lapse" and ordered the constitution of a strong commission to look into the matter.
This raises a lot of questions. Foreign dignitaries visiting Pakistan would be hesitant to talk at the PM House? They will pause before saying anything delicate. They will ask themselves a hundred times whether these conversations are being recorded.
The country's highest executive office has been "spied upon" in a "severe breach of cyber security."
Despite established procedures, intelligence agencies are unaware of how the PM House has been bugged for months. Furthermore, according to sources, the Intelligence Bureau told Pakistan's Prime Minister Shehbaz Sharif about the hacking that came to light a few weeks ago. The dark web announced that it would soon release additional information. "I will be providing ALL files sooner for undisclosed reasons," the website claimed. There will be no more haggling and offers to sell the data will be taken. According to the dark web, the audios contain interactions with journalists, chats with government officials, conversations with the top military leaders and personnel, personal and official deals, and interactions between the first family and other families, among other types of material. Additionally, it stated that it has audio recordings of talks that may be used as evidence. These discussions included those with serving judicial appointments, with foreign dignitaries, and instructions or commands given by staff. "Hopefully this release will bring betterment to Pakistan," the dark web letter said.
The country's highest executive office has been "spied upon" in a "severe breach of cyber security."
According to a hacker, Aamer Liaquat and Judge Arshad Malik were slain by Imran Khan. The hacker further asserted that Imran Khan's order locked the former DG FIA Bashir Memon in the PM House restroom. Imran Khan vowed to make Memon follow his instructions. In response to the claim of the hacker, Memon acknowledged that Khan used abusive language toward PML-N Vice President Maryam Nawaz, which had enraged him. Memon continued that at this point, PM Azam Khan's then-principal secretary grabbed his hand, led him out of the room, and locked him in the restroom. Then, according to Memon, "Azam Khan scolded me for my conduct with the prime minister." A powerful committee has been established in order to investigate audio leaks from the PM House that have called into question the government's cyber security.
Multiple audio leaks have also been shared online, igniting fresh political debate around the PTI's claim of a US conspiracy. In one of the audio leaks, the former prime minister was apparently heard discussing how to utilize the US cypher problem to further the party's narrative. A private TV channel claimed that the committee, which consists of federal ministers and the leaders of security services, will be in charge of overseeing the inquiry into audio leaks from the Prime Minister's House (PMO). Azam Nazir Tarar, the minister of law and justice, Sherry Rehman, the minister of climate change, Asad Mehmood, the minister of communications, Aminul Haque, the director-general of inter-services intelligence (ISI), the director-general of the intelligence bureau (IB), and the cabinet secretary will also serve on the high-level committee, which will be led by interior minister Rana Sanaullah. The investigation will also include co-opted members who are technical specialists from the Pakistan Telecom Authority, FIA, ISI, and National Information Technology Board.
The committee will be in charge of monitoring and analyzing the PM Office cyber security breach and making sure that it is fully investigated within seven days. The notification stated that "[they] will review the current cyber security protocols of the Prime Minister's House/Office and suggest immediate measures and an action plan to develop foolproof security systems and a digital eco-system that insulates the PM's Office/cyberspace House from all kinds of intrusion (in seven days)". The committee will review current cybersecurity and e-safety policies and procedures, analyze the current vulnerabilities and strengths of government agencies, and reevaluate the dangers posed by various electronic devices such as tablets, smartphones, WiFi, and other cyber devices. "And offer ways to strengthen government agencies' resistance against cyberattacks."
The committee has also been given instructions by the prime minister to establish a legal framework for a secure cyber environment for government offices and to make suggestions within 15 days on how to safeguard sensitive data from crucial ministries.
What is the Deep and Dark Web?
The dark web is a secret network of websites that can only be accessed with a specialized web browser. It is used to maintain the privacy and anonymity of internet activity, which is useful for both legal and illegal uses. The use of it for extremely criminal activities has also been reported, even though some people use it to avoid government censorship. There are millions of websites, databases, and servers that are all active around the clock on the vast Internet. However, the sites that can be accessed using search engines like Google and Yahoo are only the tip of the iceberg when it comes to the so-called "visible" Internet (also known as the surface web or open web). The non-visible Web is surrounded by a number of terminologies, but if you're going to venture off the beaten track, it's important to understand how they differ.
The "visible" surface layer is the open web, often known as the surface web. The open web would be the top part that is above the sea if we were to continue to picture the full web as an iceberg. According to statistics, this group of websites and data accounts for less than 5% of the entire internet. These are all frequently visited public-facing websites that can be accessed with conventional browsers like Google Chrome, Internet Explorer, and Firefox. Websites are typically identified by registration operators like ".com" and ".org" and are simple to find using well-known search engines. Because search engines can index the web through visible links (a technique known as "crawling" because the search engine moves through the web like a spider), it is possible to locate surface web websites. About 90% of all websites are found on the deep web, which is underground. This would be a portion of an iceberg that was submerged and was much larger than the web on the surface. In fact, the size of this hidden network makes it impossible to determine precisely how many pages or websites are open at any given time. If we continue with the comparison, big search engines could be compared to fishing boats that can only "grab" webpages at the surface. Everything else, including scholarly publications, exclusive databases, and additional illegal content, is out of your grasp. The area of the deep web that is known as the dark web is also included.
The Global Cybersecurity Index (GCI) placed Pakistan 94th overall and 18th out of 38 Asia-Pacific nations, trailing Bangladesh, Sri Lanka, and India
Cybersecurity is a big challenge for Pakistan
Pakistan has taken many steps to compete with other nations in the digital arena, but problems with governance, data privacy, and cybersecurity have slowed down its progress. The Global Cybersecurity Index (GCI) placed Pakistan 94th overall and 18th out of 38 Asia-Pacific nations, trailing Bangladesh, Sri Lanka, and India, according to the report "Transforming Digital Government in Pakistan". Recurrent cyberattacks throughout the previous five years are to blame for the low rating. The government hasn't done well when it comes to building trust by guaranteeing the security of citizens' personal information. Numerous Pakistani organizations, including the Federal Board of Revenue (FBR), Careem, PTV Sports, the website of Sindh High Court, Patari, K-Electric, NADRA, PITB, Meezan Bank, and Bank Islami, have experienced cyberattacks, and last month Sensitive data of the Securities and Exchange Commission of Pakistan (SECP) was also stolen.
The research states that gaining the population's trust "requires effective data privacy procedures in the government's public monitoring activities" with regard to figuring out the population and its need to establish a threshold for trust. To that end, the government made advances by enacting the Prevention of Electronic Crimes Act (PECA), 2016, which lays out penalties for offenders or criminals who are accused of gaining unauthorized access to personal data. Through its National Response Centre for Cyber Crime, the Federal Investigation Agency (FIA) also enacts legislation regarding penalties under the PECA filing (NR3C). While the cyber security policy- 2021 must be put into full effect.
Numerous Pakistani organizations, including the Federal Board of Revenue (FBR), Careem, PTV Sports, the website of Sindh High Court, Patari, K-Electric, NADRA, PITB, Meezan Bank, and Bank Islami, have experienced cyberattacks, and last month Sensitive data of the Securities and Exchange Commission of Pakistan (SECP) was also stolen.
Cyber Security Framework
The U.S. Department of Commerce's NIST is the National Institute of Standards and Technology. The NIST Cybersecurity Framework assists companies of all sizes in comprehending, managing, and reducing their cybersecurity risk as well as safeguarding their networks and data.

In his executive order for Improving Critical Infrastructure Cybersecurity, former US President Barack Obama called for greater collaboration between the public and private sectors in recognizing, analyzing, and managing cyber risk. In response, the NIST Cybersecurity Framework was developed. NIST has emerged as the gold standard for evaluating cybersecurity maturity, detecting security weaknesses, and adhering to cybersecurity legislation even when compliance is optional.
To assist firms in managing their cybersecurity risks, the Framework incorporates best practices and industry standards. It offers a standard language that enables workers at all organizational levels and at all supply chain nodes to become aware of one another's cybersecurity concerns.

Hacking and precautionary measures for your phone
One or more of these can indicate that your phone has been hacked:
Your phone quickly loses battery. Malicious code can be used by malware and fraudulent apps, which can consume a lot of power.
Your phone is operating unusually slowly. A compromised phone may be giving the hacker's dubious applications complete access to its computing power. Your phone can become quite slow as a result of this. Sometimes the symptoms include unexpected restarts and freezing crashes.
Your other online accounts show unusual behavior. A hacker who gains access to your phone will attempt to take control of your valuable accounts. Look for password reset requests, strange login URLs, or new account signup verifications on social media and in your email.
You discover strange texts or calls in your logs. Your phone may be being tapped by hackers using SMS malware. Alternatively, they can pretend to be you in order to steal private information from your loved ones. Both methods leave traces, like outgoing mail, so keep a watch out.
While there are a number of ways a hacker might access your phone and take sensitive and private data, here are some suggestions to prevent that from happening:
On your phone, install comprehensive security software. Over time, we've developed the good habit of doing this on our laptops and computers. Our phones are not at all. Installing security software on your smartphone could provide you with the first line of defense against attacks as well as some of the additional security features discussed below. Update your mobile device's apps. In addition to installing security software, the main strategy to keep you and your phone safe are to stay up to speed with updates.
Updates can close security holes used by thieves to launch their malware-based attacks. Additionally, those updates can help keep your phone and apps running smoothly while also introducing new, helpful features. Use a VPN to stay safe when traveling. Public Wi-Fi, found in places like hotels, airports, and even libraries, is one way that thieves might access your phone. Since these networks are public, all of your online activities, including banking and password usage, are visible to other users. By using a VPN, you may make a public network private and keep your online activity private from other users.
Make use of a password manager. Another important line of defense is the use of strong, distinctive passwords. The temptation to use (and re-use) shorter passwords arises from the fact that managing the hundreds of strong, unique passwords we need to manage the numerous accounts we have might feel like a chore. Because one password can unlock numerous accounts, hackers adore this situation. Try using a password manager instead, which can both generate these passwords for you and store them securely. One will be present in comprehensive security software. Avoid using public chargers. A public charging station makes charging look so easy and secure. However, some cybercriminals have been found to "juice jack" charging stations by inserting malware. They "jack" your passwords and personal information as you "juice up." How should power on the road be handled then? Consider a portable power source that you can pre-charge or use AA batteries to power. They are reasonably priced and simple to locate.
Keep a vigilant eye on your phone. Additionally, it's crucial to avoid having your phone actually stolen, as some hacks only take place when a phone ends up in the wrong hands. This is an excellent time to lock your phone with a password or PIN and enable device tracking so you can find it if you need to or even remotely wipe it. A step-by-step manual for remotely wiping devices is made available to iOS users by Apple, and an Android user manual is made available by Google. Encrypt your phone. Your calls, messages, and important data can be safeguarded by encrypting the data on your mobile device to prevent hacking. You can scroll to the bottom of Touch ID & Passcode, check if data protection is enabled, and see if your iPhone is encrypted to find out if it is (typically this is automatic if you have a passcode enabled). Depending on the phone model, Android users can automatically encrypt their data.
Lock your SIM card. The SIM card that is used to identify you as the owner and link you to your cellular network can be locked, much like your phone. It keeps your phone from being used on any other network but your own by locking it. If you have one, you can lock your iPhone by following these easy instructions. Go to the manufacturer's website to learn more about other platforms.
When not in use, turn off your Bluetooth and Wi-Fi. Consider it as closing a door that was once open. A dedicated hacker with the right tools can launch a variety of attacks against devices with open and discoverable Wi-Fi and Bluetooth. Similarly, while not a hack, some stores use Bluetooth technology to track your whereabouts within a store for marketing purposes, so turning it off might sometimes preserve your privacy. Both are simple to turn off via your settings, and many smartphones also give you the option to do so from a pull-down menu on your home screen.
Avoid using app stores from outside sources. In order to help ensure that apps are safe and secure, Google Play and Apple's App Store have systems in place to review and vet them. That procedure might not be in place for third-party websites. In reality, as part of a larger deception, certain third-party websites may purposefully host dangerous programs. Even though hackers have developed techniques to get through Google and Apple's review procedures, there is still a much higher probability of downloading a secure program from these sources than from any other. Additionally, Google and Apple swiftly remove harmful programs when they are found, further enhancing the security of their app marketplaces.
Using the built-in phone tapping codes is a quick and simple way to find the problem and solve it. With these fast codes, you can have access to confidential data about the security of your device. Utilizing them is as simple as calling a number; the phone will instantly recognize your actions and provide you with the information. To learn more about these vital cell phone codes and hacks, continue reading:
- Code to show your IMEI: *#06#
- Show if anyone catches my unanswered calls: *#61#
- Code to check call forwarding status: *#62#
- Code to check for call forwarding number: *#67#
- Code to check all call forwarding information: *#004#
- Code to check if the phone is tapped: *#21#

